FHM fence factory provides a variety of Chain Link Fencing Temporary Fencing for your supplying chain/warehouse.You could have a multiple choice here.
Chain Link Mesh Temporary Fence Chain Link Fencing Temporary Fencing Chain Link Fencing Temporary Fencing,Temporary Chain Link Fence,Portable Chain Link Fence,Temporary Dog Fence DINGZHOU FEIHONG METAL MESH CO.,LTD , https://www.fhmfencing.com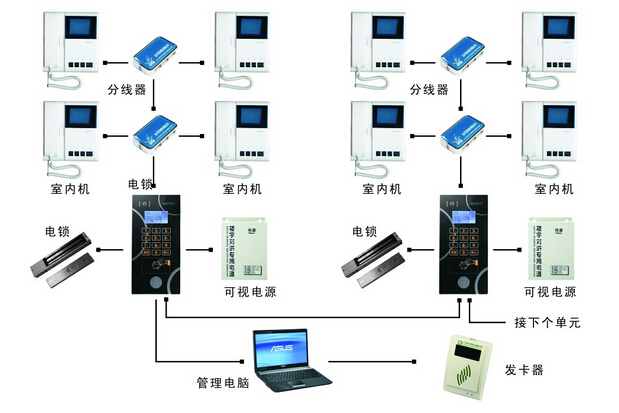
1. Unauthorized Access Data Class Attack The main purpose of unauthorized access data type attacks is to obtain user data and/or signaling data transmitted in the wireless interface. The methods are as follows:
Eavesdropping user data - obtaining user information content eavesdropping signaling data - acquiring network management information and other information tracking for active attacks - obtaining mobile user identity and location information, enabling wireless tracking of passive transport stream analysis - guessing User communication content and destination active transport stream analysis - access information
2. Unauthorized access to network service-type attacks In an unauthorised access to network service-type attacks, an attacker spoofs a network by impersonating a legitimate mobile user identity, gains authorized access to network services, and evades payment, and is also spoofed by mobile users. Pay for the attacker.
3. Threat data integrity class attacks Threat data integrity class attacks are targeted at user data streams and signaling data streams in wireless interfaces. Attackers modify, insert, delete, or retransmit these data streams to implement spoofed data receivers. The purpose is to achieve some kind of attack intention.
Insecure factors on the network side In the building intercom mobile communication network, the composition of the network side is more complicated. It not only contains many functional units, but also the communication media between different units is not the same. Therefore, there are also some insecure factors that cannot be ignored in the security mobile communication network - such as wireless eavesdropping, identity spoofing, tampering with data and service repudiation. According to the type of attack, there are four categories as follows:
1. Unauthorized access to data types The main purpose of attacking unauthorized data access attacks is to obtain user data and/or signaling data transmitted between network-side units. The specific methods are as follows:
Eavesdropping on user data - obtaining user communication content eavesdropping signaling data - obtaining security management data and other information facilitating active attacks, counterfeit communication receivers - obtaining user data, signaling data, and other information that facilitates active attacks Flow analysis - obtaining access to information illegally accessing data stored in the system - obtaining data stored in the system, such as authentication parameters of legitimate users, etc.
2. Unauthorized access to network service attacks The main purpose of unauthorised access to network service attacks is to access the network and evade payment. The specific manifestations are as follows:
Counterfeit and legal use - access to the authorized fake service network accessing the network service - access to the network service, fake home network - obtain the authentication parameters that can impersonate the legitimate user identity, abuse the user's authority - enjoy the network service abuse network service authority without paying - Obtaining illegal profits
3. Threat data integrity class attacks Building intercom mobile communication network threats Data integrity attacks include not only those threatening data integrity attacks in the wireless interface, but also the communication interface between the BSS and the MSC may be a wireless interface. Moreover, it also includes a wired communication network, and the specific performance is as follows:
Manipulating user data streams - accessing network service access or deliberately interfering with communication manipulation signaling data streams - gaining access to network services or intentionally interfering with communication counterfeit communication participants - gaining access to network services or intentionally interfering with communication manipulation downloadable applications - Interfering with the normal operation of the mobile terminal, manipulating the mobile terminal - the normal operation of the mobile terminal, the data stored in the network unit - obtaining access to the network service intentionally interferes with the communication
4. After the service repudiation-type attack service, the repudiation-type attack is that the communication has occurred after the communication, thereby avoiding payment or evading responsibility. The specific performance is as follows:
Paid repudiation - refusal to pay The sender denies - unwilling to pay for the sent message service Receiver repudiation - unwilling to pay for the received message service
There are various insecurities in the radio communication network - such as wireless eavesdropping, identity spoofing, tampering with data and Post-service repudiation. These security factors directly affect the security of the community, so how to avoid these problems, it depends on the efforts of various manufacturers.
Height x Length : 6` x 10`
Frame Tube : 32 x 2.0mm
Wire Diameter : 3mm
Mesh Size : 50 x 50mm
Material: Hot dipped galvanized wire & tube
Typical Applications
1> Construction Site
2> Security Project
3> Crowd Control
Probe into the Unsafe Factors of Building Intercom System
[ Huaqiang Security Network News ]
With the advancement of science and technology and the demand for mobile communication services, building access intercom systems are being applied to various communities. At present, the building access control intercom mobile communication network will continue to develop continuously, and in the future, it will be able to more perfectly realize the communication service demand of the majority of building intercom mobile communication users.
Insecure factors in the wireless interface In the building intercom mobile communication network, all communication between the mobile station and the fixed network is transmitted through the wireless interface, but the wireless interface is open, and the perpetrator can eavesdrop through the wireless interface. The channel obtains the transmission information therein, and can even modify, insert, delete or retransmit the message in the wireless interface to achieve the purpose of spoofing the mobile user identity to deceive the network terminal. According to the type of attack, it can be divided into three types: unauthorized access data, unauthorized access to network services, and threat data integrity.